Jul 12, 2023 | by Sosou Editor | Other Call
1. Phone number 915-373-5195 Basic information
2. Caller Information and International Formats
3. Don't know what to do with the call from 9153735195?
4. Comments from users on phone numbers
5. Some of the lesser-known scams that have recently spread in the United States
6. Articles you may be interested
The phone number 9153735195 is the Wireless phone number registered with the operator Sprint Spectrum L.p.. Usually assigned to mobile phone users. The phone number 915-373-5195 has been registered at El Paso (Texas).
The telephone number with area code 915 is widely used as a mobile phone line for individual users. Phone charges will be charged during the call. Answering calls is free.
Phone number 915-373-5195 was registered with the number search service on Jul 12, 2023, viewed 21 times, and searched 32 times.
Phone number has a user rating of 4.0 out of 5.
El Paso
▶ Latest Review: In this section, we will see some of the famous hackers and how they become famous.
Jonathan James
Jonathan James was an American hacker. He is the first Juvenile who send to prison for cybercrime in the United States. He committed suicide on 18 May 2008, of a self-inflicted gunshot wound.
In 1999, at the age of 16, he gained access to several computers by breaking the password of a NASA server and stole the source code of International Space Station, including control of the temperature and humidity within the living space.
Kevin Mitnick
He is a computer security consultant, author, and hacker. He infiltrates his client's companies to expose their security strengths, weaknesses, and potential loopholes. In the history of the United state, he was formerly the most wanted computer criminal.
From the 1970s up until his last arrest in 1995, he skillfully bypassed corporate security safeguards and found his way into some of the most well-guarded systems like Sun Microsystems, Nokia, Motorola, Netcom, Digital Equipment Corporation.
Mark Abene
Mark Abene is an American Infosec expert and Entrepreneur. He is known around the world by his pseudonym Phiber Optik. Once, he was a member of the hacker groups Legion of Doom and Master of Deception. He was a high profile hacker in the 1980s and early 1990s.
He openly debated and defended the positive merits of ethical hacking as a beneficial tool for the industry. He is also expert in penetration studies, security policy review and generation, on-site security assessments, systems administration, and network management, among many others.
Robert Morris
Robert Morris was the creator of the Morris Worm. He was the first computer worm to be unleashed on the Internet. The Morris Worm had the capability to slow down computers and make them no longer usable. Due to this, he was sentenced to three years probation, 400 hours of community service and also had to pay a penalty amount of $10,500.
Gary McKinnon
Gary McKinnon is a Scottish systems administrator and Hacker. In 2002, he was accused of the "biggest military computer hack of all time". He has successfully hacked the network of Navy, Army, Air Force, NASA system of the United States Government.
In his statement to the media, he has often mentioned that his motivation was only to find evidence of UFOs and the suppression of "free energy" that could potentially be useful to the public.
Linus Torvalds
Linus Torvalds is a Finnish-American software engineer and one of the best hackers of all the time. He is the developer of the very popular Unix-based operating system called as Linux. Linux operating system is open source, and thousands of developers have contributed to its kernel. However, he remains the ultimate authority on what new code is incorporated into the standard Linux kernel.
Torvalds just aspire to be simple and have fun by making the world's best operating system. Linus Torvalds has received honorary doctorates from University of Helsinki and Stockholm University.
Kevin Poulsen
Kevin Poulsen is an American former Black-hat hacker. He is also known as Dark Dante. He took over all the telephone lines of radio station KIIS-FM of Los Angeles, guaranteeing that he would be the 102nd caller and win the prize of a Porsche 944 S2.
Poulsen also drew the ire of FBI, when he hacked into federal computers for wiretap information. As a result of this, he was sentenced for five years. He has reinvented himself as a journalist.
▶ According to the votes of anonymous users, we temporarily classify the phone number 915-373-5195 as: Other Call. This classification is not authoritative and is for reference only.
▶ To call from overseas:
① [00] International Access Code
② [1] Country Code United States
③ [915] Area Code
④ [373] Phone Prefix
⑤ [5195] Line Number
To dial the US phone number "915-373-5195"
Please dial 00-1-915-373-5195 ・ +1-915-373-5195
▶ For missed calls or other unknown caller numbers. Nor can you always relax. Do not call back without confirmation. Don't reveal anything about yourself in the conversation.
▶ If you answer the call and ask "yes" or "no" hang up.
If someone asks you to answer a question, hang up.

*The scammers claim they called the tax office and demanded a large amount be paid immediately. Otherwise, they threaten an immediate account blocking.
* Clone accounts of young women on Instagram" accounts are linked to a website (similar to OnlyFans, a popular platform that offers erotic and pornographic content) that promises sexually explicit content that requires the entry of a credit card.

*CEO fraud, scammers pretend to be company bosses and usually contact employees of a company with manipulated e-mail addresses; then they instruct the employees to make payments.
*Cyber criminals try to lure potential victims into a trap by promising large prizes, an inheritance from a stranger, or by pretending that the computer has been hacked.
*A new scam is currently being used to defraud pensioners of over a hundred dollars. Callers hope to convince pensioners to send them "care boxes with information". It costs $99 or eve
*Scammers Pretend to be government officials and claim they intercepted a package from you in the post office. The scammers claim that you allegedly ordered something suspicious and now they need information from you.
*The information about 915-373-5195 in the article comes from the Internet, and it cannot be concluded that it is malicious.
We strive to make the content and information on this website as accurate as possible. However, the information may be out of date and the number owner changes frequently.
▶ To help you understand what types of scams there are and keep them in mind, here are some of the most common scams. Coronavirus Scam, Online Shopping Scam, Lotteries, Sweepstakes, Contest Scam, Investment Scam, Tax Scam, Dating & Love Scam, Bank, Credit Card, Online Account Scam, Job & Employment Scam, Advance Loan Scam.
▶ If you encounter scams, you can greatly reduce your chances of becoming a victim by:
*Don't install any software or go to websites that scammers tell you.
*Please do not answer or call back unknown phone numbers.
*Do not confirm any information over the phone if the caller is pretending to know something about you.
*Do not give unknown people bank details or data such as your ID number, your address or customer accounts with passwords.
*Please do not pay registration fees or shipping costs for so-called free products or prizes.
*Don't be intimidated by threats from scammers posing as office officials. Give them your information or transfer money.
*Please do not use gift cards, prepaid debit cards or bank transfers to make purchases on unconfirmed websites.
▶ If you have been the victim of fraud, please contact the police or the consumer advice center immediately.
If you have shared information, contact the relevant service company and make the necessary changes.
It is important not to panic even in the event of damage and to be able to take the right "handling" and "reaction" immediately.
▶ I Received a Call From an Unknown Number 📞915-308-9944, What Should I do?
▶ I Received a Call From an Unknown Number 📞915-269-7636, What Should I do?
▶ Prevent Harassing Calls 915-284-4074 and How to Respond Correctly
▶ I Received a Call From an Unknown Number 📞915-216-9753, What Should I do?
▶ I Received a Call From an Unknown Number 📞915-226-0680, What Should I do?
▶ Warning⚠️ 9158387289 Hazard Introduction and Treatment Methods
▶ I Received a Call From an Unknown Number 📞915-731-4611, What Should I do?
▶ Warning⚠️ 9153561881 Hazard Introduction and Treatment Methods
Published on:Jul 12, 2023 Updated on:May 23, 2024
Due to the nature of this service, there is no guarantee that all phone number reviews are true or accurate. Please contact us if the phone number is unavailable, ownership has been transferred, or the review information is inaccurate.
*Please help us keep your information current and complete. You can correct the information. (We will update the information after we confirm the authenticity)
Not all reviews can be verified, so we cannot guarantee the accuracy or reliability of reviews

In this section, we will see some of the famous hackers and how they become famous.
Jonathan James
Jonathan James was an American hacker. He is the first Juvenile who send to prison for cybercrime in the United States. He committed suicide on 18 May 2008, of a self-inflicted gunshot wound.
In 1999, at the age of 16, he gained access to several computers by breaking the password of a NASA server and stole the source code of International Space Station, including control of the temperature and humidity within the living space.
Kevin Mitnick
He is a computer security consultant, author, and hacker. He infiltrates his client's companies to expose their security strengths, weaknesses, and potential loopholes. In the history of the United state, he was formerly the most wanted computer criminal.
From the 1970s up until his last arrest in 1995, he skillfully bypassed corporate security safeguards and found his way into some of the most well-guarded systems like Sun Microsystems, Nokia, Motorola, Netcom, Digital Equipment Corporation.
Mark Abene
Mark Abene is an American Infosec expert and Entrepreneur. He is known around the world by his pseudonym Phiber Optik. Once, he was a member of the hacker groups Legion of Doom and Master of Deception. He was a high profile hacker in the 1980s and early 1990s.
He openly debated and defended the positive merits of ethical hacking as a beneficial tool for the industry. He is also expert in penetration studies, security policy review and generation, on-site security assessments, systems administration, and network management, among many others.
Robert Morris
Robert Morris was the creator of the Morris Worm. He was the first computer worm to be unleashed on the Internet. The Morris Worm had the capability to slow down computers and make them no longer usable. Due to this, he was sentenced to three years probation, 400 hours of community service and also had to pay a penalty amount of $10,500.
Gary McKinnon
Gary McKinnon is a Scottish systems administrator and Hacker. In 2002, he was accused of the "biggest military computer hack of all time". He has successfully hacked the network of Navy, Army, Air Force, NASA system of the United States Government.
In his statement to the media, he has often mentioned that his motivation was only to find evidence of UFOs and the suppression of "free energy" that could potentially be useful to the public.
Linus Torvalds
Linus Torvalds is a Finnish-American software engineer and one of the best hackers of all the time. He is the developer of the very popular Unix-based operating system called as Linux. Linux operating system is open source, and thousands of developers have contributed to its kernel. However, he remains the ultimate authority on what new code is incorporated into the standard Linux kernel.
Torvalds just aspire to be simple and have fun by making the world's best operating system. Linus Torvalds has received honorary doctorates from University of Helsinki and Stockholm University.
Kevin Poulsen
Kevin Poulsen is an American former Black-hat hacker. He is also known as Dark Dante. He took over all the telephone lines of radio station KIIS-FM of Los Angeles, guaranteeing that he would be the 102nd caller and win the prize of a Porsche 944 S2.
Poulsen also drew the ire of FBI, when he hacked into federal computers for wiretap information. As a result of this, he was sentenced for five years. He has reinvented himself as a journalist.
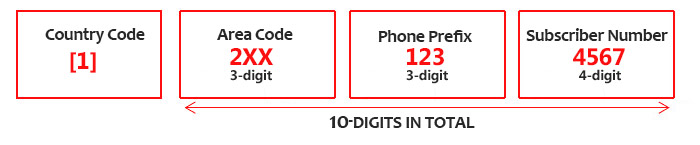
Area codes in the United States are between 2 and 9. Since the international telephone area code of the United States is 1, and within the United States, the prefix 1 indicates long-distance calls, so the telephone area code of the United States does not start with 1. There are also area codes without a location reference, such as the toll-free 800. The US area code represents which city or region it is.
2XX 3XX 4XX 5XX 6XX 7XX 8XX 9XXIn the U.S. and Canada, phone numbers usually consist of 11 digits—1 country code, 3 area code, 3 phone prefix and 4 line number. The country code of USA is +1. It is unique for every country. Area codes direct your calls to a large, broad area. A phone prefix is a smaller area within the area, such as a city. The line number is the specific call you are trying to reach. The following figure shows the structure of the phone number:In the U.S. and Canada, phone numbers usually consist of 11 digits—1 country code, 3 area code, 3 phone prefix and 4 line number. The country code of USA is +1. It is unique for every country. Area codes direct your calls to a large, broad area. A phone prefix is a smaller area within the area, such as a city. The line number is the specific call you are trying to reach. The following figure shows the structure of the phone number:
Due to the nature of this service, there is no guarantee that all phone number reviews are true or accurate. Please contact us if the phone number is unavailable, ownership has been transferred, or the review information is inaccurate.
*Please help us keep your information current and complete. You can correct the information. (We will update the information after we confirm the authenticity)
Look up an address from a list of popular area codes
Wir stellen Ihnen für jede deutsche Stadt ein Branchenbuch zur Verfügung